
When I encounter a problem on a VoIP network that needs troubleshooting, I just wish that I had microscopic X-ray vision, like a superhero who is able to peer into the subatomic level of things.
It would be so advantageous to be able to instantaneously see what is going on with transmissions on the network.
When you experience voice quality issues, one way or choppy voice, or call setup problems, it would be great to be able to see, are the voice packets arriving? How are they arriving?
What kind of signaling is getting through and what is being blocked and where?
These are questions I wish I had instant access to, and this is what port mirroring is all about.
Well, barring X-ray vision as a solution, the next best thing is to use a packet sniffer such as Wireshark to be able to look at the “sub-packet” level of the network for VoIP troubleshooting.
Wireshark as a tool can be intimidating at first, and I know this because this was the case for me. But once you get the hang of it, you will truly see what a powerful tool it is and it will quickly become one of the primary instruments in your troubleshooting toolbox.
Build pro IOS configs. FAST.
In this article, we’ll focus on how to prepare your network for capturing VoIP packets using Wireshark.
Contents
How do you capture voice packets using SPAN?
In order for Wireshark to capture VoIP packets, there are two fundamental requirements. First, the computer on which Wireshark is installed must be connected to a port on the network, and second, this network port must be configured appropriately to send the voice packets to the computer for analysis. When troubleshooting for VoIP, there are two ways to configure such a network port. The first involves using the Switched Port Analyzer (SPAN) feature on a Cisco switch, while the second involves enabling the “Span to PC” port configuration parameter on the IP phone itself. Which method you use depends upon the nature of the problem you are troubleshooting and the procedure you are choosing to apply
Note here that the feature, when applied on a switch, uses the acronym “SPAN”, while when indicated within the web interface of the CUCM uses the word “Span” instead.
Port Mirroring using SPAN
SPAN is the term used for this feature on Cisco switches. The more general term this feature is known by is port mirroring, and it’s available on multiple platforms. Here, we’ll be focusing on Cisco switches. Regardless of the name, this is a feature available on switches allowing the collection of packets being exchanged on a network to take place on a specific port of that switch. When enabled, SPAN will send a copy of all of the packets that are seen on one switch port to a network monitoring connection on another port on that switch. Take a look at the following diagram.
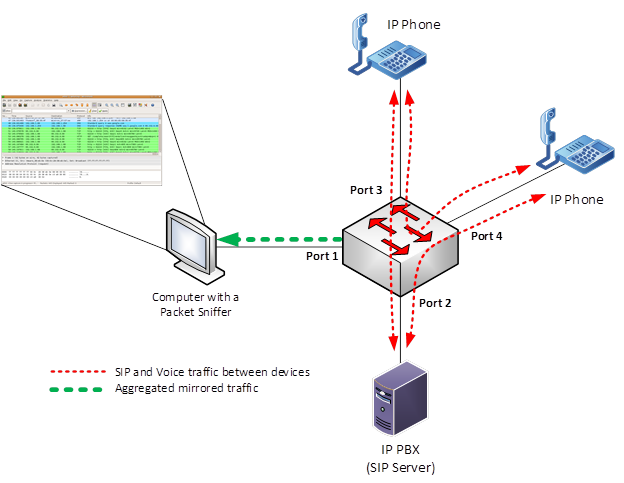

Using the above scenario, Port 1 can be configured as the mirrored port, or the monitoring port. This is the port on which a computer running Wireshark would be connected. Ports 2, 3 and 4 are then configured as source ports for the port mirroring, that is, they are designated as ports whose traffic is copied to the mirrored port.
The result is that all traffic on Ports 2, 3 and 4, whether incoming or outgoing, is replicated and sent to Port 1. The packets will be collected at the network card of the computer allowing it to capture, store and later analyze them.
When to use SPAN to capture VoIP packets
The SPAN feature is ideal when the VoIP packets you want to capture are not confined to a single IP phone, but are found within the core of the network itself. This is the case when you want to capture voice packets going to and coming from the voice gateway, or when you want to examine SIP signaling that takes place between multiple endpoints and the CUCM.
SPAN configuration on Cisco IOS switches
On most Cisco IOS switches, the configuration for SPAN involves the following steps:
- Create a SPAN session.
- Specify which port is the source or monitored port. This is the port whose traffic is going to be monitored. Note that multiple source ports can be configured.
- Specify which port is the destination, or monitoring port. This is the port where all of the traffic on the source ports will be copied and sent to. There can only be one destination port per session. This is also the port on which you will connect the Wireshark computer.
In the following example, we’ll configure ports GigabitEthernet 0/3, 0/4, and 0/7 as the monitored ports, and GigabitEthernet 0/1 as the destination port.
Switch(config)# monitor session 1 source interface gigabitethernet0/3 Switch(config)# monitor session 1 source interface gigabitethernet0/4 Switch(config)# monitor session 1 source interface gigabitethernet0/7 Switch(config)# monitor session 1 destination interface gigabitethernet0/1
Note here that the above commands fall under a specific monitoring session, specifically, session 1. It is possible to create multiple monitoring sessions within a switch, but each one can have only a single destination port, and each destination port can only belong to a single monitoring session.
You can verify this configuring using the following command:
Switch# show monitor session 1 Session 1 Source Ports: RX Only: None TX Only: None Both: Ge0/3, Ge0/4, Ge0/7 Source VLANs: RX Only: None TX Only: None Both: None Destination Ports: Ge0/1 Switch#
The output here shows that GigabitEthernet ports 0/3, 0/4, and 0/7 are source ports and that both egress and ingress packets on these ports are being captured and copied to the destination port. It also shows that the destination port is GigabitEthernet 0/1.
There are several additional and useful parameters that can be used to narrow down the types of packets captured. The following output shows some of these parameters:
Switch(config)#monitor session 1 source interface fa0/1 ? , Specify another range of interfaces Specify a range of interfaces both Monitor received and transmitted traffic rx Monitor received traffic only tx Monitor transmitted traffic only
Using the context sensitive help, we can see that you can specify a range of interfaces with a comma to separate them, or you can specify a range of interfaces. You can also indicate if you want to capture ingress traffic (rx), egress traffic (tx), or both. Capturing both directions is the default, and this is why the output in our configuration indicates this.
Port Mirroring using SPAN – what to keep in mind
When configuring SPAN on a switch, you should keep the following in mind:
- Wireshark will capture all of the packets “seen” on a particular monitoring source including data packets. So you will have to perform some filtering of the resulting captured packets to view the particular voice packets you are interested in analyzing.
- The source of a monitoring session can be a switchport, a routed port, an EtherChannel port, an access port, a trunk port, a VLAN interface, or a whole VLAN. Choose whatever is most appropriate for what you want to capture.
- The more sources you have the more packets will be captured, and the more difficult it will be to find the packets that you are interested in. Make sure you choose your source ports wisely and the direction of traffic you want to capture to minimize the capturing of needlessly excessive traffic. This will make your analysis easier, and will also avoid oversubscribing the monitor port resulting in lost (and uncaptured) packets.
- When you configure a destination port, its previous configuration is lost, and it cannot be used to forward normal traffic.
Port Mirroring using ‘Span to PC’
The Span to PC feature allows you to configure a Cisco IP phone so that all of the voice traffic it sends and receives can be copied to the PC port on the device. It’s kind of like the SPAN feature, but for an IP phone. The PC connected to the PC port of the phone can capture all of the packets sent to and from the phone simply by running Wireshark. The following diagram describes such a scenario.
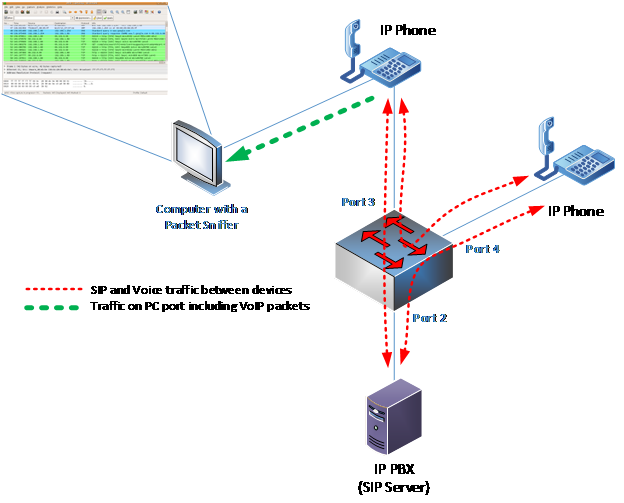

When to use it ‘Span to PC’ to capture VoIP packets
The Span to PC feature should be used when you want to analyze the voice packets sent to and from a specific phone. This feature is useful when troubleshooting issues that are isolated to the specific device on which it is being configured.
Span to PC configuration
The Span to PC feature is somewhat more simplistic than the SPAN feature. In order to enable it, you must log in to the CUCM web administration, and go to the “Product Specific Configuration Layout” section of the “Phone Configuration” page of the particular device you want to configure.

Under this section, find the “Span to PC Port” option.


It may help to do a “find in page” on your browser and search for the text to find it, as, depending on the phone model, there may be hundreds of configuration parameters.
Once you find it, verify that it is set to “Enabled”.
Keep in mind that in order for the Span to PC feature to function, the following must also be set:
- “PC Voice VLAN Access” must be set to “Enable”
- “PC Port” must also be enabled
The result of these settings is that all packets sent to and from the IP Phone on the phone’s interface are copied and sent to the PC port as well. As a result, they can be captured using Wireshark installed on the PC connected to that port.
Port Mirroring using ‘Span to PC’ – what to keep in mind
When configuring Span to PC feature, you should keep the following in mind:
- Wireshark will capture all of the packets coming to and from the NIC of the PC, including data packets that it sends and receives anyway. So you will have to perform some filtering of the resulting captured packets to view the voice packets and analyze them.
- The Span to PC feature is not supported on older phones such as the 7940 and 7960
- It is best practice to keep this feature disabled for security purposes when not in use.
Conclusion
SPAN and Span to PC are port mirroring features that provide you with superheroic X-ray vision to see what is happening with your voice packets. Once these features have been configured, the next step is to prepare Wireshark to begin capturing and storing packets for analysis. We’ll take a closer look at this preparation and analysis of captured packets in an upcoming article.



Build pro IOS configs. FAST.